Home/ Blog / How to Effectively Identify and Monitor Major IT and Cybersecurity Risks
The rise in cloud computing, fintech solutions, and increased reliance on interconnected systems has exposed banks and financial organizations to various vulnerabilities that can have far-reaching consequences. Understanding and managing these risks is crucial for the success and security of modern banking businesses.
We will investigate the key aspects of identifying and monitoring major IT and cybersecurity risks and highlight how the Predict360 IT Risk Assessment (ITRA) Solution can help businesses respond to these challenges effectively.
Types of Major IT and Cybersecurity Risks
Before diving into risk identification and monitoring matters, let’s understand some examples of major IT and cybersecurity risks organizations face today.
Phishing Attacks
Phishing attacks are deceptive attempts to trick individuals into divulging sensitive information, such as usernames, passwords, or financial data. Attackers often use cleverly crafted emails, websites, or messages that appear legitimate, making it challenging for individuals to discern the malicious intent. These attacks can lead to data breaches, financial losses, and reputational damage.
Malware Attacks
Malware attacks encompass various malicious software, including viruses, spyware, and worms. These programs are designed to infiltrate computer systems, compromise data security, and disrupt operations, resulting in data loss, system downtime, and potential financial losses.
Ransomware
Ransomware is a particularly insidious form of malware that encrypts and locks an organization’s data. The hacker then demands a ransom for its release. Paying the ransom does not guarantee data recovery. Organizations find themselves in a challenging position if they fall victim to such an attack, leading to significant financial losses and reputational damage.
Weak Passwords
Weak passwords, such as easily guessed or commonly used ones, present a pervasive IT and cybersecurity risk. Attackers can exploit weak passwords to gain unauthorized access to systems and sensitive data. This risk is mitigated through robust password policies and multi-factor authentication.
Insider Threats
Insider threats involve employees, contractors, or business partners who get access to an organization’s systems and data and misuse their privileges. This can range from intentionally stealing sensitive information to unintentionally causing data breaches. Insider threats require careful monitoring and employee awareness programs to mitigate the risk effectively.
Steps for Identifying IT and Cybersecurity Risks
The Information Systems Audit and Control Association (ISACA) has outlined a six-step process for identifying and cataloging potential IT and cybersecurity risks. The six steps include the following:
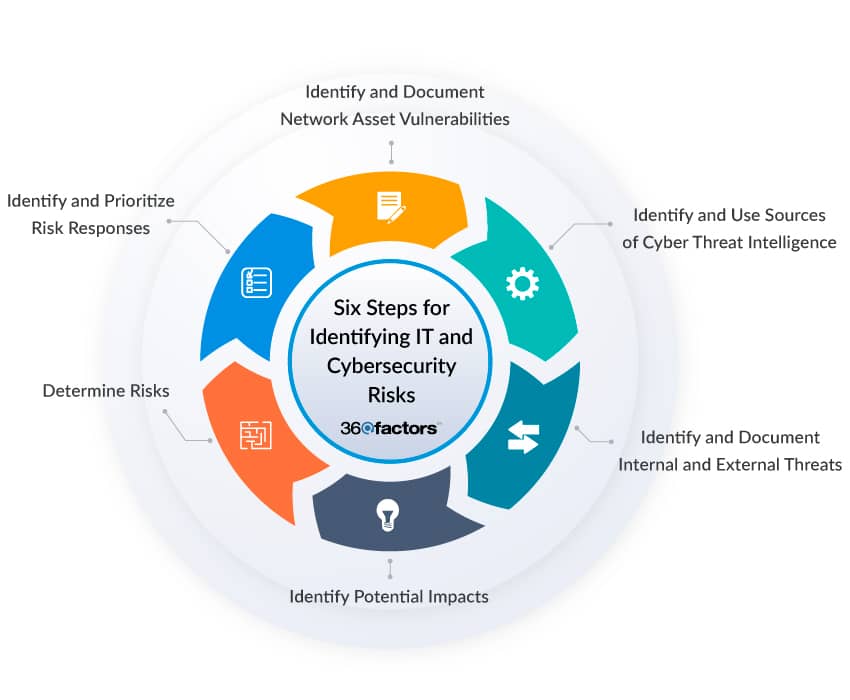
Identify and Document Network Asset Vulnerabilities
The first step is to identify and document vulnerabilities in your network assets. This involves creating a thorough inventory of all your IT assets, including hardware, software, and data.
Vulnerabilities can be anything from outdated software with known security flaws to misconfigured settings. Scan your systems regularly to identify and prioritize vulnerabilities based on severity.
Identify and Use Sources of Cyber Threat Intelligence
To stay ahead of emerging threats, it’s essential to identify and utilize sources of cyber threat intelligence. This includes subscribing to threat intelligence feeds, participating in information sharing and analysis centers (ISACs), and monitoring reputable cybersecurity news sources.
By staying informed about the latest cyber threats and attacks, you can proactively address potential risks.
Identify and Document Internal and External Threats
Internal and external cybersecurity threats should be carefully documented. Internal threats can arise from employees, contractors, or other individuals with access to your systems, while external threats include malicious actors like hackers and cybercriminals.
Develop a threat profile for your organization, outlining potential IT threats and their motivations.
Identify Potential Impacts
In this step, consider the potential impacts of the identified threats and vulnerabilities. Assess how a successful attack or system failure could affect your organization’s operations, financial stability, and reputation.
By understanding the potential impact of each threat, you can prioritize your risk assessment efforts.
Use Threats, Vulnerabilities, Likelihoods, and Impacts to Determine Risk
Combine the information gathered from the previous steps to assess the inherent risks associated with each identified threat and vulnerability. Use a structured methodology to assign likelihood and impact ratings to each risk.
For example, you can use a risk matrix to classify risks as high, medium, or low based on their likelihood and impact. This will help you prioritize your response efforts.
Identify and Prioritize Risk Responses
The final step in the process is to identify and prioritize risk responses. Once you have assessed the risks, determine how to address them. Responses may include implementing security controls, developing incident response plans, or transferring risks through insurance. Prioritize your responses based on the severity of the risks and your organization’s risk tolerance.
Significance of IT Risk Monitoring
Monitoring IT and cybersecurity risks is not just best practice, it’s a strategic necessity for businesses. There are several compelling reasons why investing in cybersecurity assessments and continuous monitoring is crucial.
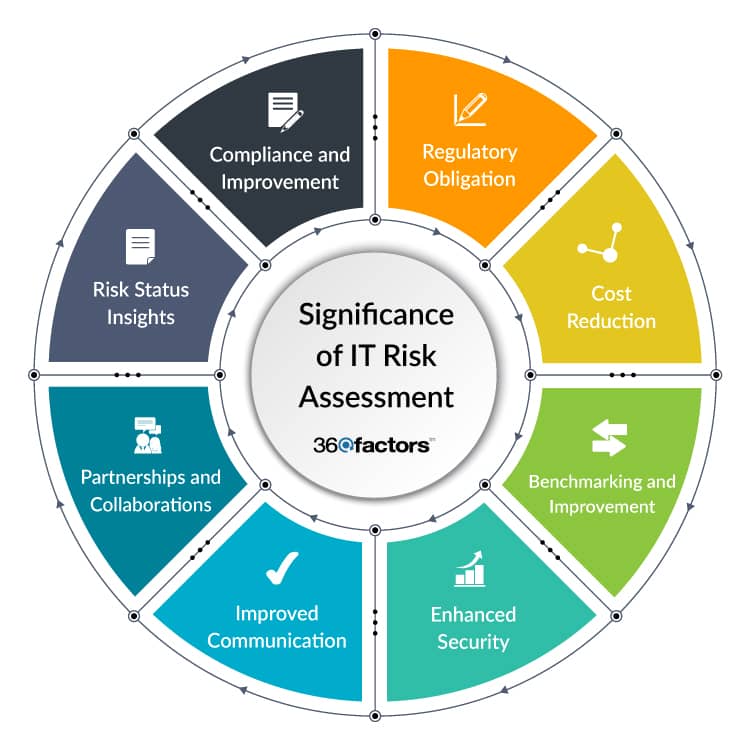
Regulatory Obligation
The financial industry has specific regulatory requirements, and cyber risk assessments are mandatory in some cases. For instance, GDPR (General Data Protection Regulation) requires “companies processing personal data” to perform a cyber risk assessment.
Compliance with such regulations is not just a legal requirement but also essential for maintaining trust with your customers.
Cost Reduction
Identifying and mitigating cybersecurity threats through continuous monitoring can help prevent security incidents.
This proactive approach reduces the likelihood of breaches and incidents, saving your organization money in the long term. Preventing an incident is far more cost-effective than dealing with post-incident losses.
Benchmarking and Improvement
Cyber risk assessments are not a one-off event. The first assessment serves as a benchmark or barometer for your organization’s cybersecurity posture.
Subsequent assessments are opportunities for improvement. By continually monitoring and updating assessments, you can measure progress and identify areas that need strengthening.
Enhanced Security
Risk assessment and monitoring help your organization proactively avoid security breaches and other incidents. By identifying, monitoring, and addressing vulnerabilities, you fortify your cybersecurity defenses and reduce the likelihood of system breaches.
Improved Communication
Active cyber risk monitoring can enhance communication between departments, stakeholders, and third-party vendors. It fosters a common understanding of the organization’s cybersecurity posture and ensures everyone is on the same page when it comes to risk and security measures.
Partnerships and Collaborations
Continuous monitoring of cybersecurity risks facilitates collaboration with partners and third parties. It aids in developing and improving risk mitigation plans, security standards in data processing agreements, and other comparable contracts. It helps establish a common baseline for security standards.
Risk Status Insights
Continuous IT risk monitoring also provides valuable insights into the cyber risk status of business partners, third parties and associates. This information is critical for making informed decisions about collaborations and ensuring the security of your ecosystem.
Compliance and Improvement
Cybersecurity risk monitoring helps achieve compliance and provides a robust baseline for your organization’s security posture.
A risk monitoring report offers a comprehensive overview of your security status, findings, and recommendations for strengthening your defenses and supporting continuous improvement in security measures.
Conclusion
Addressing IT and cybersecurity risks is a continuous process that requires a comprehensive approach. Organizations can mitigate these risks effectively and safeguard their business operations by identifying potential IT risks, assessing their impact and likelihood, and continuously monitoring them through security tools, audits, and regular assessments.
One invaluable tool that can aid in this process is Predict360 IT Risk Assessment Software. It is a comprehensive IT risk assessment application that allows businesses to monitor cybersecurity threats and system vulnerabilities effectively. It offers real-time IT risk assessment, compliance management, incident response, and comprehensive reporting, making it an invaluable asset for businesses seeking to protect their IT and cybersecurity infrastructure.
In a world where the digital landscape is constantly evolving, taking a proactive approach to identifying and monitoring major IT and cybersecurity risks is not just a good practice; it’s a necessity for the long-term success and security of your organization.
Request a Demo
Complete the form below and our business team will be in touch to schedule a product demo.
By clicking ‘SUBMIT’ you agree to our Privacy Policy.



