Home/ Blog / How Banks Can Develop an Effective Framework for IT and Cyber Risk Assessment
Cybersecurity and IT risk management have become quite critical for modern banking operations. Increasing reliance on technology has brought in a new era of convenience and efficiency for customers, allowing them to utilize banking services with greater freedom and accessibility. However, digitized banking operations have also increased the risks associated with cyber threats and IT vulnerabilities.
As the guardians of sensitive customer data and financial assets, banks must establish a robust IT and cyber risk assessment framework to ensure their clients’ security. In this article, we will look into the critical elements of creating such a framework and consider Predict360 IT Risk Assessment (ITRA), a cybersecurity risk assessment software designed to streamline and enhance the IT risk assessment process.
The Need for an IT and Cyber Risk Assessment Framework
A robust IT and cyber risk assessment framework is essential for banks as it provides a structured approach for identifying, assessing, and mitigating technological and cybersecurity risks. A well-designed framework can protect customer data, financial assets, and the bank’s reputation while meeting compliance obligations.
Here are some of the main reasons why an IT risk assessment framework is necessary;
- Banks collect and process a vast amount of sensitive customer data. A practical IT risk assessment framework is the first line of defense against data breaches and unauthorized access, ensuring that customer information remains confidential and secure.
- Cybercriminals often target the financial assets of banks. A robust IT risk assessment framework helps banks identify vulnerabilities and implement safeguards to protect their financial resources from theft or fraud.
- Trust is a fundamental aspect of the banking industry. A breach of trust due to a lapse in cybersecurity measures can have long-lasting, detrimental effects on a bank’s reputation. An IT risk assessment framework helps banks maintain customer trust by ensuring that the security and integrity of their systems are built on a solid foundation.
- Governments and regulatory bodies have set up stringent legal requirements for data security and privacy for the financial sector. Non-compliance can result in severe penalties. Risk assessment frameworks help banks adhere to these regulations and avoid costly fines.
Advanced Elements of IT and Cyber Risk Assessment Framework
The U.S. National Institute of Standards and Technology has outlined the following model as the fundamental elements of an IT risk assessment framework.
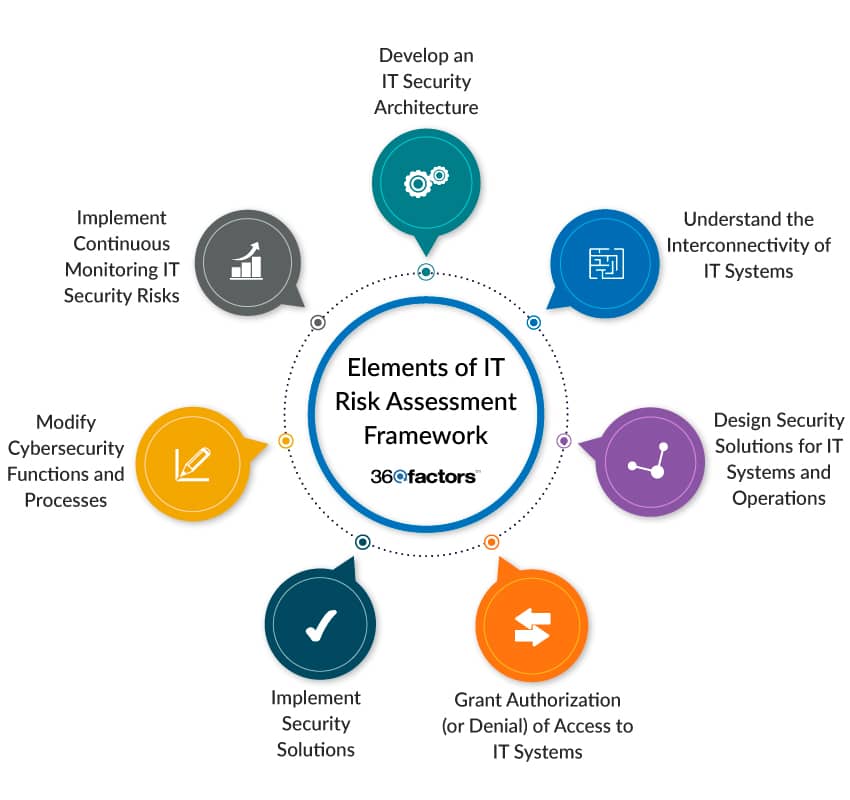
Development of an IT Security Architecture
The foundation of an effective IT risk assessment framework begins with the development of a robust information security architecture. This offers a blueprint for creating secure information systems and ensuring data confidentiality, integrity, and availability.
Understanding the Interconnectivity of IT Systems
To minimize risks associated with interconnected IT systems, it’s essential to define clear and stringent interconnection dependencies. This includes specifying how different IT systems interact and ensuring these connections adhere to security standards.
Design of Security Solutions for IT Systems and Operations
The design phase involves creating comprehensive security solutions for IT systems and their operational environments. This encompasses selecting the appropriate security controls, IT products, firewalls, suppliers, and contractors to meet the specific IT security requirements.
Authorization (or Denial of Authorization) to Access IT Systems
Authorization to access sensitive information systems is a critical step in the IT risk assessment framework. This phase determines whether access to an IT system meets the necessary security standards to function safely. If it falls short, denial of authorization is crucial until security controls are in place.
Implementation of Security Solutions
Implementation involves putting security solutions and controls into practice. To ensure effectiveness, the selected security measures must align with established security requirements and standards.
Modification of Cybersecurity Functions and Processes
There are instances when it’s necessary to modify business functions and processes to address newly discovered threats and vulnerabilities in the IT systems or until compensating controls are implemented. This adaptive approach ensures that the IT systems remain resilient to evolving risks.
Monitoring IT Security Risks
The journey doesn’t end with implementation. Continuous monitoring and periodic risk audits are vital components of IT risk assessment. This ensures that security solutions remain effective and resilient, adapting to emerging threats and vulnerabilities in a constantly changing landscape.
Develop an Effective Framework for IT and Cyber Risk Assessment
With the foundational elements of the framework laid out, the path to developing an effective IT and cyber risk assessment framework involves a series of strategic steps:
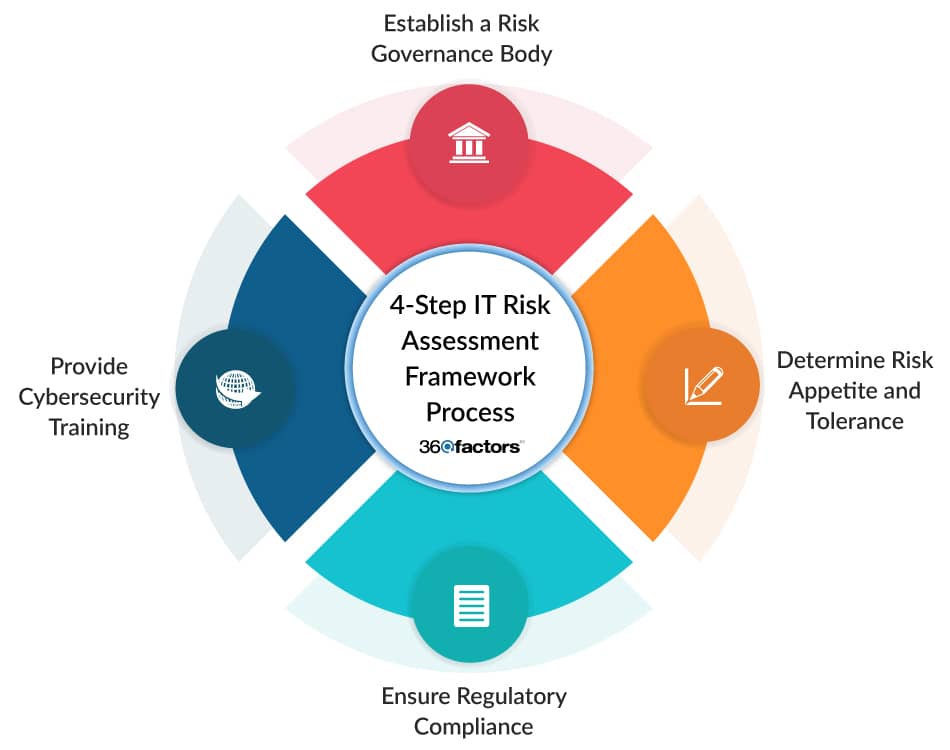
Risk Governance Body
Successful risk management necessitates establishing a dedicated team or department with the expertise to oversee IT and cyber risk. These experts serve as the vigilant protectors of the bank’s digital assets.
Risk Appetite and Tolerance
Banks must set their risk appetite and tolerance level, which determines the threshold for IT risk assessment. Risk appetite defines the parameters for risk-taking, aligning the IT risk assessment framework with the broader objectives of the bank.
Regulatory Compliance
Cybersecurity regulations are continually evolving, given the rapid developments in fintech and banking digitalization. A well-structured IT risk framework must proactively align with changing regulations, safeguarding the bank against non-compliance issues, which could result in fines or reputational damage.
Cybersecurity Training
With advancing technology, the human factor remains pivotal in cybersecurity. A well-informed and trained staff are a core component of the bank’s IT defense, as human error often plays a significant role in cybersecurity incidents. Continuous education is a proactive defensive measure against these potential pitfalls.
Implementation of IT Risk Assessment Through Predict360 ITRA
An IT and cybersecurity risk assessment framework provides the structure and strategy for IT risk assessment. However, its efficacy is magnified when complemented with appropriate technology.
Predict360 ITRA stands out for its efficiency and adaptability. This comprehensive, AI-augmented risk assessment solution simplifies and enhances IT and cyber risk assessment for banks, offering a range of benefits:
- 360-Degree Visibility: Predict360 ITRA provides a panoramic view of IT and cyber risks, allowing banks to identify vulnerabilities and threats across their entire organizational ecosystem. It’s like having an eagle-eye view of the battlefield, enabling more strategic responses.
- Efficient Risk Assessment: Predict360 ITRA streamlines the cybersecurity risk assessment process, making it more efficient. This allows banks to respond proactively to potential IT risks, significantly reducing the time between threat identification and mitigation.
- Customizable Framework: Predict360 ITRA can be tailored to suit the specific needs and risk appetite of individual banks. This flexibility ensures that the IT risk assessment framework is not a one-size-fits-all solution but one that adapts seamlessly to each institution’s unique needs and objectives.
In conclusion, the IT and cyber risk assessment framework is a cornerstone of a bank’s strategy to safeguard its digital assets, customer trust, and financial integrity. By identifying, assessing, and mitigating risks and implementing the right technology solutions, banks can effectively protect themselves in an ever-changing digital landscape.
Predict360 ITRA offers an intelligent and adaptable solution for banks looking to fortify their IT and cyber risk assessment capabilities.
Request a Demo
Complete the form below and our business team will be in touch to schedule a product demo.
By clicking ‘SUBMIT’ you agree to our Privacy Policy.



