Home/ Blog / How do IT & Cybersecurity Risk Trends Impact Enterprise Strategies
The world of IT and cybersecurity is shifting at a swift velocity in the existing era, bringing new challenges and opportunities for enterprises across the US. As we go into the complex landscape of cyber risk trends, it is paramount for companies to stay ahead of the latest developments and work proactively to protect their digital assets.
The Imperative of Cybersecurity in Modern Enterprise Strategies
Technology integration in every phase of business operations has depicted cybersecurity as the foundation stone of enterprise approaches. The possibility of cyber incidents having a negative impact goes beyond financial penalties. It can be particularly detrimental to an enterprise’s brand image and destroy customer trust.
Cyber Risk Trends: A Critical Component of Strategic Planning
Understanding cyber risk trends is essential for the long-term success and resilience of organizations. As cyber risks become more severe and persistent, the requirement for complete and adaptive cybersecurity metrics also increases. Companies must adopt an integrated approach, considering not just the technological attributes but also the procedural and human aspects of cybersecurity.
Let’s discuss the top IT/cybersecurity risk trends that are expected to impact enterprise strategies as per an investigation by Gartner. These trends range from ransomware attacks and vulnerabilities in enterprises to the challenges posed by cloud security and the capabilities of AI-powered cyber risk assessment solutions.
Top Cyber Risk Trends for 2023
- Exposure to Threat Management
- Resilience in Identity Systems
- Verification of Cybersecurity Protocols
- Integration of Cybersecurity Platforms
- Revamping the Security Operational Structure
- Modular Approach to Security
- User-Centered Security Framework
- Advancement in Staff Management for Security
- Enhanced Governance and Oversight by the Board
Enabling Organizations to Address Key Priorities
The recognized cybersecurity trends help enable organizations to address four key priorities, ensuring a robust and responsive security posture:
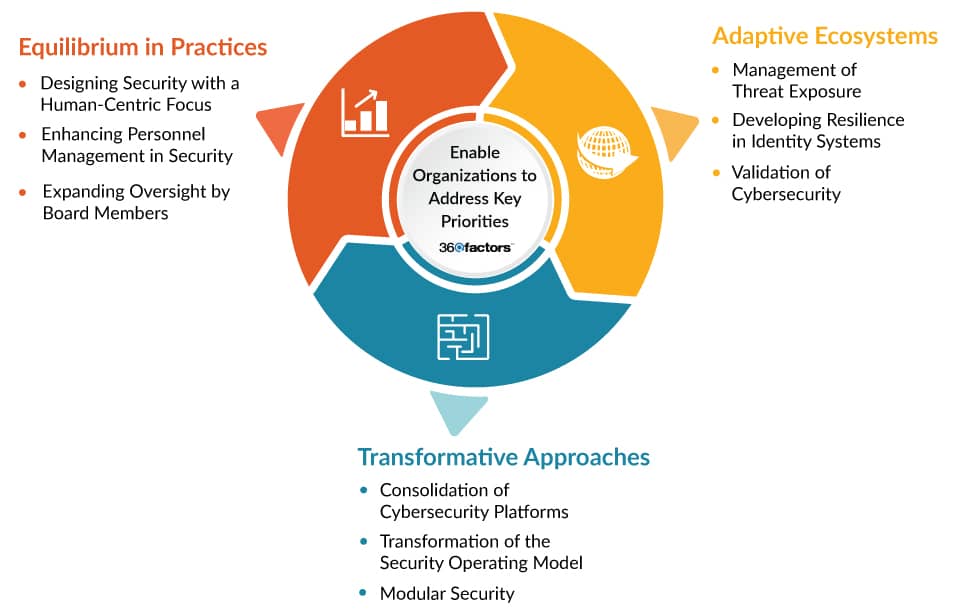
Theme 1: Adaptive Ecosystems
These trends advance efforts in resolving risks by adopting a continuous approach to managing risks and validating cybersecurity measures. This theme of cyber risk trends aims to strengthen detection and response capabilities, as well as determine more resilient ecosystems.
Management of Threat Exposure
Involves a systematic, successful strategy to refine the main concern for cybersecurity optimization perpetually. This practice evolution augments the understanding of increasing risk exposure and addresses vulnerabilities in security postures.
Developing Resilience in Identity Systems
Introduces the concept of digital immune systems to identity management, attempting to curtail defects and failures through balanced investments in both prevention and detection and response for IT risk assessment.
Validation of Cybersecurity
This cyber risk trend combines various techniques, procedures, and tools to validate how potential attackers might exploit identified threat experiences and how protective systems and processes would respond.
Theme 2: Transformative Approaches
These trends endeavor to strike a balance between operational simplicity and the necessity to extend coverage across a progressively expansive attack surface.
Consolidation of Cybersecurity Platforms
It aims to reduce complexity, streamline operations, and enhance staff efficiency. Organizations opt for fewer vendors, expanding improved integration, and more features from an associated set of products.
Transformation of the Security Operating Model
This cyber risk trend involves restructuring technological and analytical obligations, expanding the scope and speed of cybersecurity risk decision-making, and accelerating positive business outcomes.
Modular Security
Establishes an approach where cybersecurity controls are effortlessly integrated into architectural models, applied at a modular level within composable technology executions, guaranteeing protection across all parts of a business process.
Theme 3: Equilibrium in Practices
These trends highlight the necessity of sustaining a weighed focus on people, processes, and technology in terms of Risk assessment software to mitigate cybersecurity risks successfully.
Designing Security with a Human-Centric Focus
Puts employee experience in the foreground, beyond just technical regards, throughout the controls management lifecycle. The cyber risk trend develops insights from behavioral sciences and user-experience disciplines. This method aims to reduce insecure employee behavior.
Enhancing Personnel Management in Security
Transfers the focus towards human-centric approaches for talent acquisition and retention. Chief Information Security Officers (CISOs) embracing this approach witness upgrading in functional and technical maturity.
Expanding Oversight by Board Members
Guarantees that cybersecurity remains a significant part of governance and oversight activities, imposing an increase in cybersecurity expertise at the board level moving forward.
Theme 4: Implementing IT Risk Assessment Solution
In the face of progressing cyber risk trends, organizations are in extreme need of innovative solutions to help them stay ahead of possible risks. Predict360 IT Risk Assessment Software is designed to address these challenges, arranging a comprehensive and AI-augmented approach to managing IT risks and controls within an enterprise framework.
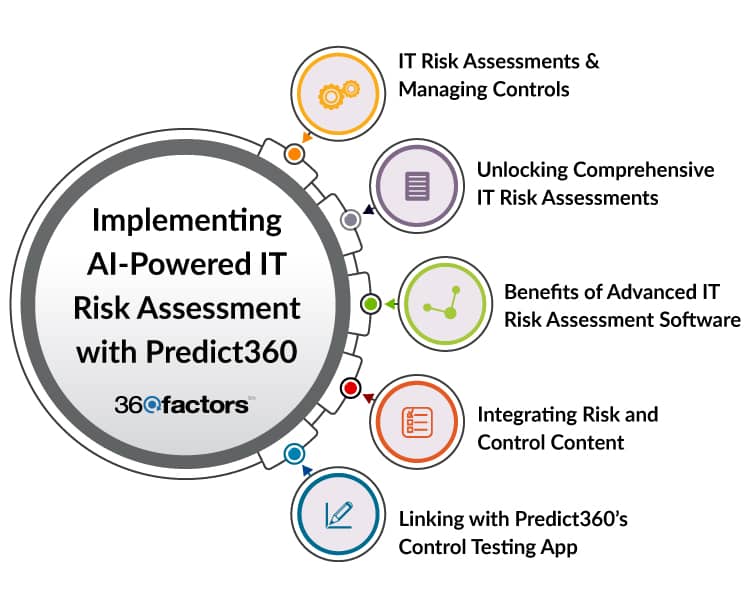
Streamlining IT Risk Assessments & Managing Controls
Predict360 offers a streamlined workflow for documenting and analyzing IT risks, ensuring organizations can maintain a consolidated risk and control taxonomy across various business areas.
Unlocking Comprehensive IT Risk Assessments
Built on industry-based enterprise risk management techniques, Predict360 is particularly tailored for financial entities, resounding with the sophisticated cyber risk trends of the banking and finance sectors. It provides real-time insights into IT Risk Assessment progress and risk ratings, standardizes risk and control taxonomies, and generates enterprise-level reports from data across different business units.
Advantages of Advanced IT Risk Assessment Software
Predict360 enhances scalability, allowing organizations to handle increased data and more complex risk scenarios as they grow. It ensures accuracy and consistency in risk assessments, reducing the chances of human error and oversight.
Integrating Risk and Control Content
This IT risk assessment tool offers optional risk libraries that can be added to an organization’s risk and control taxonomy, providing a rich resource for risk management and facilitating the challenges of cyber risk trends. These can include standardized libraries such as the NIST Cybersecurity, CRI Cybersecurity Profile and GLBA Information Sharing risks.
Connecting with Predict360’s Control Testing Application
For organizations looking to dive deeper into risk management, the Predict360 Control Testing application extends the capabilities of the Risk Management and Assessment tool. It oversees control activities, streamlines testing workflows, and offers optional control tests integrated into the software.
Conclusion
To effectively manage the challenging environment of IT and cybersecurity, identifying and preparing for emerging risks and trends is essential. The cyber risk trends we have explored display the significance of companies adopting a comprehensive and vigilant approach to cybersecurity, safeguarding readiness against current challenges and future uncertainties.
Developing responsive ecosystems and reorganizing strategic approaches are crucial to achieving a robust cybersecurity posture. By embracing the trends and strategies discussed, organizations enhance their capacity to respond to cyber threats, safeguard digital assets, and maintain stakeholder trust.
Integrating AI-powered IT risk assessment systems, such as Predict360, is instrumental in this journey. These tools provide real-time insights, a comprehensive risk assessment process, and advanced reporting capabilities, empowering organizations to navigate cybersecurity complexities with confidence and precision. The adoption of such advanced solutions into enterprise strategies ensures proactive risk management and the strengthening of defenses to oversee cyber risk trends.
Request a Demo
Complete the form below and our business team will be in touch to schedule a product demo.
By clicking ‘SUBMIT’ you agree to our Privacy Policy.



